Connector for Microsoft SharePoint - Authentication
Integration module Connector for Microsoft SharePoint / New data source / Continue to SharePoint authentication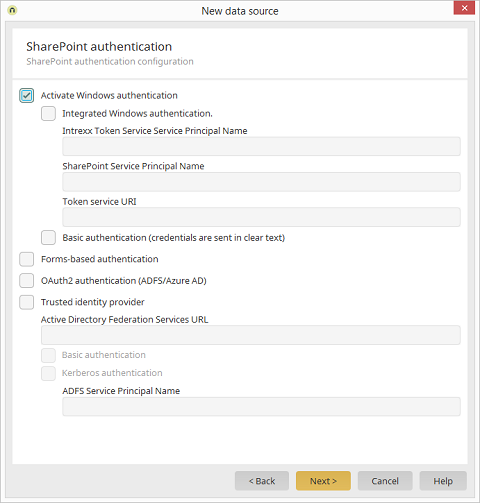
Windows basic authentication
Activate this setting for the basic or Kerberos authentication.Windows integrated authentication
The option Windows integrated authentication provides you with the ability to use Single Sign On. Based on Kerberos tickets, the Kerberos authentication provides the Intrexx users with Single Sign On access to the SharePoint server. To ensure successful authentication with Kerberos, please take note of the following foundational requirements:- The Intrexx Portal needs to operate with integrated authentication. This can be setup in the Users module and in the menu Configuration.
- The users from your Active Directory must be added accordingly to Intrexx. You can conveniently import users in the Users module by going to the menu User / User and group import…. Please make sure that at least one user is kept in the group Administrators so that you can continue to administrate the system.
- The server, where Intrexx is installed, requires the group rule Delegation in the Active Directory (Trust this computer for delegation to any service (Kerberos only)).
- All clients and servers must be members of the same domain.
-
The Intrexx portal and the SharePoint server muss belong to
the local intranet zone from the perspective of the
client (browser).
The SPNEGO authentication must be activated in the browsers.
In Internet Explorer for example, the option
Automatic log-on with current username and
password must be selected in the security settings of
the used zone. Additionally, the option
Enable Integrated Windows Authentication must be
activated in the advanced settings.
When using Google Chrome, the hostnames of the Intrexx SharePoint
servers need to be added to a white list in the registry. You can
find more information about this here:
https://dev.chromium.org/administrators/policy-list-3#AuthNegotiateDelegateWhitelist
With Firefox, you need to add the servers to the white list in the Firefox configuration (about:config) under the keys:
andnetwork.negotiate-auth.trusted-urisnetwork.negotiate-auth.delegation-uris - To provide Kerberos tickets, the Intrexx Kerberos Token Provider Service must be installed in the Internet Information Server that is used to communicate with Intrexx. Further information on this topic can be found here.
You need to specify a so-called Service Principal Name (SPN) for the authentication to be successful. The SPN contains information about the service for which a Kerberos ticket should be created. This ticket is needed for the Internet Information Server of the Intrexx portal server.
The SPN is usually compiled as follows:
http/<Computer-DNS-Name>@<KERBEROS_REALM>
Computer-DNS-Name: Fully qualified hostname (e.g. mycomputer.mycompany.com)
KERBEROS_REALM: The domain is usually entered in capitals. (e.g. MYCOMPANY.COM)
The SPN from the example above would look like this:
http/mycomputer.mycompany.com@MYCOMPANY.COM
Basic authentication
With the Basic authentication, the username and password of a SharePoint user are requested in Intrexx and sent as the header in the HTTP request to SharePoint. This is the simplest login method and should only be used in connection with HTTPS because otherwise, credentials are transferred without being encrypted.Forms-based authentication
The forms-based authentication allows users to log in using a SharePoint login form. With this option, a login form will be shown in Intrexx to the user when they access the SharePoint data for the first time. Intrexx then carries out the authentication using the SharePoint Web service (or /_vti_bin/authenticate.asmx) in the background.OAuth2 authentication (ADFS/Azure AD)
All information regarding this topic can be found here.Trusted identity provider
The option Trusted identity provider can be used to perform an authentication using an SAML-conforming identity provider. Intrexx currently only supports Microsoft Active Directory Federation Services (ADFS) as an identity provider.The following prerequisites apply when using ADFS as authentication:
- The ADFS server must be installed and configured in SharePoint.
- The ADFS server has to support basic and/or Windows integrated authentication.
- The Intrexx Kerberos Token Service must be installed and configured for Windows integrated authentication with ADFS. Further information on this topic can be found here.
Active Directory Federation Services URL
In this field, the URL for the ADFS server's login page is specified, as it is sent from the SharePoint server to the client browser via redirect. This could look something like this:https://logon.spdev.net/adfs/ls/auth/integrated/?wa=wsignin1.0&wtrealm=urn%3asharepoint%3asp2013adfs&wctx=http%3a%2f%2fsp2013adfs.spdev.net%2f_layouts%2f15%2fAuthenticate.aspx%3fSource%3d%252F
The URL contains the three essential parameters wa, wtrealm and wctx. The required values for these parameters can be taken from your SharePoint ADFS configuration. Please note that the URL character string is already encoded in such a way that it conforms to URL.
Intrexx sends the user login details to this URL and, if the login was successful, is redirected to the SharePoint server to complete the authentication and authorization. When using basic authentication, the username and password are sent directly to ADFS. With Kerberos, a ticket will first of all be requested for ADFS using the Intrexx Kerberos Provider Service, this ticket will then be sent to ADFS. Additionally, the Service Principal Name of the ADFS server will be needed for Kerberos. Windows integrated authentication must also be activated and the SPN of the Intrexx Kerberos Token Service must be specified.
Assigning users for the authentication methods
If more than one authentication method is activated, the first available method will be selected according to the following order of priority:- Basic authentication
- Windows integrated authentication
- Forms-based authentication
- ADFS authentication
| Name | Method |
| HTTP_BASIC | Windows basic authentication |
| KERBEROS_INTREXX | Windows integrated authentication |
| SHAREPOINT_FORMS_BASED | Forms-based authentication |
| SHAREPOINT_FEDAUTH_SAML | Trusted identity provider |
Make sure you are precise when entering the name. Intrexx ascertains the method to be used from the user attribute during runtime when accessing the SharePoint data groups for the first time. If this is not available or specified, Intrexx will search for the attribute in the user groups. If it cannot be found there either, Intrexx will proceed with the order of priority listed above. The adapter must also be informed as to what the user or group attribute is called.